Configuring Azure AD Domain Services for your Active Directory Tenant
Configuring Azure AD Domain Services is fairly straight-forward process, and currently, only possible via the classic Azure Web Portal - look for this to change at some point to allow PowerShell as well.
Prior to enabling the service, you need to create an Active Directory Group with a specific name. This group will placed in the local 'Administrators' group on each of the domain-joined systems - similar to the 'Domain Administrators' group in an on-premises Active Directory.
The Domain Administrators and Enterprise Administrators groups / privileges are not available in the Azure AD Domain Services. This group simply provides local Administrator, domain-join and Group Policy management rights.
The Active Directory Group name must be 'AAD DC Administrators' in order for this to work. The following PowerShell snippet will create the group and add one Administrative user account to the group; you could also do this via the web portal:
# Note that this assumes we want to use the Azure Tenant DNS/Domain name as the ADDS domain name (NETBIOS name is limited to 15 characters)
$adminUPN = "adminusername@tenantname.onmicrosoft.com"
$cred = Get-Credential
Connect-MsolService -Credential $cred
New-MsolGroup -Description "Azure AD DC Admins" -DisplayName "AAD DC Administrators"
# Add necessary members to the domain admins group
$ADDCAdminsGroup = Get-MsolGroup | Where-Object {$_.DisplayName -eq "AAD DC Administrators"}
Add-MsolGroupMember -GroupMemberObjectId (Get-MsolUser -UserPrincipalName $adminUPN).ObjectId -GroupMemberType "User" -GroupObjectId $ADDCAdminsGroup.ObjectId
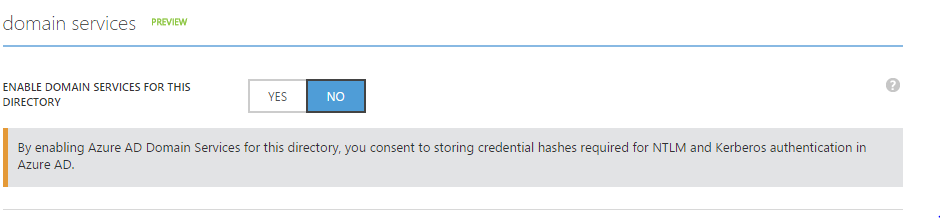
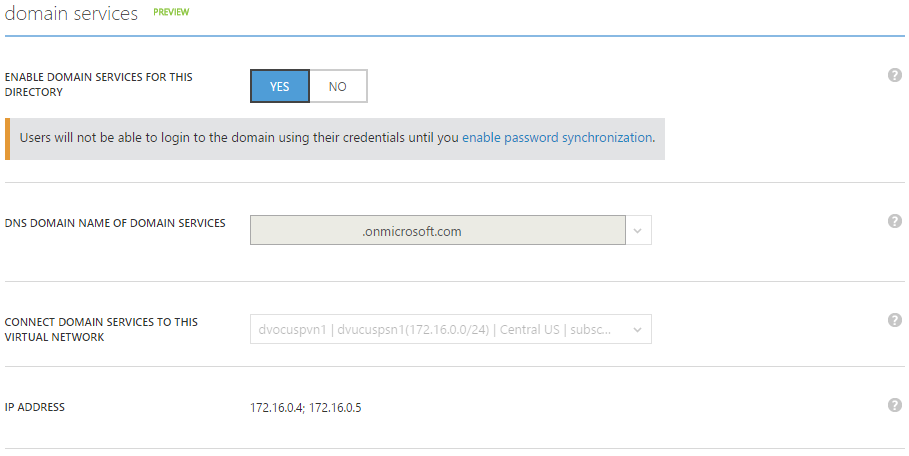
Once you've created the group, to enable the Service simply use the slider on the 'Configure' tab of the target Active Directory Domain.
You'll need to select a virtual network here (or create a new one using the portal) for which the Domain Services will be active.
The Virtual Network must be a 'regional' virtual network - existing ones may neet to be migrated, whereas all new virtual networks are created in this way.
Also, virtual networks created in the Azure Resource Manager model are not supported by Azure AD Domain Services.
The provisioning of the service has taken approximately 30 minutes, in my experience, after which the IP Addresses of the DNS Servers are displayed.
Once the provisioning is completed, you need to update the DNS settings on the Virtual network so that the Azure AD Domain Services are used - it's possible to do this via PowerShell:
$xmlNetworkConfig = (Join-Path (Get-Location).Path NetworkConfig.xml)
Get-AzureVNetConfig -ExportToFile $xmlNetworkConfig
Edit the NetworkConfig.xml file and add DnsServer nodes to the VirtualNetworkConfiguartion node for each of the DNS Servers, as below:
<NetworkConfiguration xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://schemas.microsoft.com/ServiceHosting/2011/07/NetworkConfiguration">
<VirtualNetworkConfiguration>
<Dns>
<DnsServers>
<DnsServer name="dvocuspdc1" IPAddress="172.16.0.4" />
<DnsServer name="dvocuspdc2" IPAddress="172.16.0.5" />
</DnsServers>
</Dns>
<VirtualNetworkSites>
<VirtualNetworkSite name="dvocuspvn1" Location="Central US">
<AddressSpace>
<AddressPrefix>172.16.0.0/12</AddressPrefix>
</AddressSpace>
<Subnets>
<Subnet name="dvucuspsn1">
<AddressPrefix>172.16.0.0/24</AddressPrefix>
</Subnet>
</Subnets>
</VirtualNetworkSite>
</VirtualNetworkSites>
</VirtualNetworkConfiguration>
</NetworkConfiguration>
Once that's done, update the Virtual Network configuration:
$xmlNetworkConfig = (Join-Path (Get-Location).Path NetworkConfig.xml)
Set-AzureVNetConfig -ConfigurationPath (Get-Location).Path "NetworkConfig.xml"
The Azure Active Directory tenant is now configured to use the Azure AD Domain Services; you will now be able to create VMs and join them to the Azure AD, utilize domain users for identities, and GPOs to manage the Virtual Machines.